12 Techniques to Form an Effective Permissions Strategy
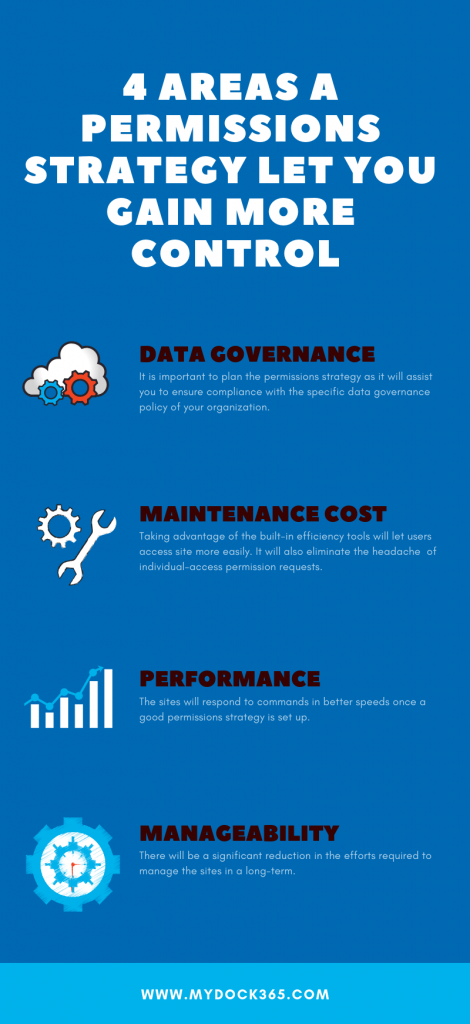
Among the numerous factors that make it unavoidable to plan a permissions strategy, it’s the benefits that amaze you the most. It can bring good manageability and performance to your site, along with compliance with the data governance policies your organization has set. There are also plenty of other factors that make planning permissions strategy a must-do process. We have explained the top factors to consider before planning a permissions strategy for a SharePoint site in the first part of this blog.

Permissions Strategy Overview
Controlling what users can access and what-not will become difficult if the permission rights are not assigned properly, . The best solution to avoid this chaos is to set up an effective permissions strategy.
We will give you 12 techniques to plan a simple yet effective strategy just like that. One good principle to follow is by ensuring the least permission privileges to each one, that let them perform the tasks assigned with ease.
- Add people to standard or default security groups along with providing access.
- Make adding most of the users to members or visitors group a basic step.
- Members group users can only add or remove documents/items.
- Visitors group users will only have read-only access to sites.
- Owners group need to have only limited users.
- Add people you trust to change the appearance, structure and site settings to Owners Group.
- Create a clean and easy to visualize hierarchy using permissions inheritance.
- Conditions like certain lists in a site with fine-grained permissions, and sites having subsites that are assigned with unique permissions, and some others with inherited permissions may cause more difficulty and more time in managing permissions.
- Users may experience slow performance while accessing sites if you decide to break permissions inheritance to use fine-grained permissions.
- A clear hierarchy of permissions and inherited permissions is what required to manage and define permissions easily.
- Keep content organized to take full advantage of the permissions inheritance.
- Segment your content using security levels. Instead of protecting sensitive data using unique permissions, create a dedicated library or site for them.
The above techniques are simple and easy to follow. Consider these tips while planning for an effective permission strategy and you will be able to get great results.
